Since some of the documents are, to this day, yet to be declassified, the complete story of how the German’s Enigma code was broken during World War II may never be completely known. The popular version, as portrayed in The Imitation Game, is that British mathematicians, chess players, and puzzle masters at Bletchley Park in England, led by the brilliant Alan Turing, worked out a method to decrypt the German military’s message traffic. The truth is far more complex and involves a cast of “hidden figures” who never received full recognition for their amazing contributions.
◊
Even a cursory examination of the history surrounding the British code-breaking operation at Bletchley Park hints at evidence that contradicts – or at least complements – the popular version of how the German Enigma code was broken. After intelligence services, in the 1990s, finally declassified many of the documents related to Bletchley, a fuller story has been long known and reported on. More recently, Sir Dermot Turing, Alan’s nephew, wrote a book to correct the record and reveal a cast of cryptologists, spies, and others who have more claim to breaking Enigma than the lone-genius Turing.
The less well-known version of events involves Polish mathematicians and a French spy master. The Poles were hidden figures much like the women in the popular movie of the same name. Their amazing cleverness allowed them to decrypt Enigma-encoded messages years before the British at Bletchley. But the accepted story of who cracked the Enigma code gained prominence because Eastern European mathematicians didn’t fit a mythical image of Oxbridge-educated linguists defeating the Nazis.
In France, a savvy espionage chief formed a crucial link between the Poles and the British. He has remained hidden from view, perhaps because he knew too much of a far messier backstory about Enigma than had been represented in popular history.
And all the principals of this shadowy story, Turing included, were subservient to the strange logic of state secrecy that forced everyone to conceal their work and accomplishments long after the war was over and their enemies defeated.
Even the Enigma machine itself is something of a hidden figure, and its origins are far more benign than one might first suspect. It’s actually a good place to begin to untangle a truer story of how Alan Turing and his team eventually achieved their well-publicized successes.
Watch Codebreaker: Alan Turing - Persecution Of A Genius on MagellanTV.
Development of Scherbius’s Enigma Machine
Hitler’s blitzkrieg tactics demanded rapid and secret communications between German commanders and their forces. Enigma would play a vital role in this new way to conduct “lightning war.” Interestingly, Enigma was not developed by the fearsome Wehrmacht of the 1930s. Instead it was invented in 1918 by Arthur Scherbius, a German engineer who planned to sell his new devices to the private sector as well as to governments.
Enigma looked like an electric typewriter with the additional feature that when a key was pressed a letter would light up (see below) indicating the newly encrypted letter. This illuminated letter would then be written down and finally transmitted by a radio operator.
 Close-up of Enigma.
Close-up of Enigma.
(Image Credit: Tomasz Mikolajczyk, via Pixabay)
There were several versions of this commercial Enigma, but they all shared one critical idea. In a classic Caesar cipher, which grade school students might use to pass secret notes to one another, thereby frustrating their teachers, each letter of the intended message is substituted for another. Scherbius’s machine, though, varied the substitutions based on the position of the letter to be encrypted.
“… correspondence will always be exposed to every spy, your letters, to being opened and copied, your intended or settled contracts, your offers and important news to every inquisitive eye ... Now, we can offer you our machine “Enigma,” being a universal remedy for all those inconveniences.” —Mid-1920s Enigma sales brochure
So, an A in a message might convert to, say, Z the first time and then the next A might switch to an X. Enigma accomplished this obfuscatory magic using three rotors connected by electric wiring that successively performed separate substitutions – think of it as three different Caesar substitution ciphers linked together.
After the first substitution, the substituted letter is transformed by the second rotor and then this process is repeated again by the third rotor. There’s one final trick that changes the substitution mapping each time: the rotors advance by a single position. Effectively, a completely new substitution scheme is in place for the next letter to be encrypted. If this is confusing, the process is shown graphically in this article.
What made Scherbius’s Enigma a truly practical device was the simplicity of the decryption: To restore the original “plain text,” the receiving operator merely keyed the encrypted letter and the correct letter lit up. That is, as long as both machines started with the same settings. We’d say today that Enigma had the equivalent of a secret password – a three-letter code used to set the initial position of each rotor.
In the mid 1920s, the German military bought and then significantly modified Scherbius’s encyrption machine. By 1930, this more complex Enigma was in the field, and the intelligence agencies of Germany’s neighbors to the east and west quickly noticed the change.
Bertrand and the French Connection
Even before the rise of Hilter, France had become increasingly wary of German intentions. A new military encryption system only further raised alarms. Unlike the British – and, as we’ll soon see, the Poles – France used far more conventional intelligence-gathering techniques.
In 1932, French agents under spy chief Gustave Bertrand struck gold when they discovered a German who had obtained documents on the top-secret Enigma coding device. He was Hans-Thilo Schmidt and was incredibly well-placed as an employee within the German military’s own cipher office. Schmidt was a man above suspicion – at least in the short term.
Bertrand personally met with Schmidt, code name “Ashes,” in Belgium to photograph the operating manual for Enigma. Schmidt’s motives were purely monetary and non-ideological, and Bertrand was only too willing to pay for the secrets. Besides Enigma, Schmidt provided significant intelligence to the French even after war started. He is considered one of the greatest spies of those years, but ultimately betrayed and arrested by the Gestapo in 1943.
When British cryptologists expressed a surprising lack of interest in the details of the Enigma machine’s operation, the wily Bertrand turned to his contacts in Polish intelligence, who were quite happy to make a deal: In return for sharing documents, the French would see the decrypted messages.
Polish Mathematicians Solved Enigma
Like their French counterparts, Polish cryptologists had quickly realized that an entirely new scheme was being used to encrypt German messages. In the early 1930s, the Polish Buro Szyfrów (cipher bureau) began recruiting mathematicians from local universities to take on the challenge. Up to this point, codebreakers were more likely to be linguists, classicists, and game players. Polish intelligence, to their credit, realized that the incredible complexity of Enigma required a different kind of thinking – mathematical thinking.
One of the students, Marian Rejewski (pronounced: Rey-EF-ski), would eventually decipher Enigma, a full seven years before the British at Bletchley Park began their efforts. He has only recently been given official recognition for his work.
Rejewski’s cryptology achievements were breathtaking. Using very clever mathematical techniques, he was able to deduce the internal wiring of the rotors – the specific substitution used in Enigma – based on carefully analyzing the encrypted German message traffic. With help from Bertrand’s plans, the Polish crypto-team was then able to build a working replica of a military-grade Enigma!
The next step was to discover the daily rotor setting for the machine – effectively, finding the password. Rejewski’s mathematical brilliance shone again. He discovered a special way to analyze German military messages, and then work backwards to deduce the likely possible rotor settings used to create the encrypted message. With their duplicated versions of the Enigma machine, the Polish cryptologists launched what computer hackers would today call a brute-force attack: They simply asked a group of their own operators to try each rotor setting from a small list until the message looked more German. It worked.
Rejewski and his team eventually became adept at guessing the daily settings as they reviewed the decrypted messages and became familiar with the senders’ habits and personality. They had an important insight that overworked and tired German operators would often use consecutive keyboard letters for the daily rotor setting – for example, QWE or UIO. They could deduce the settings without resorting to any cryptographic cleverness.

An artist’s rendering of the Polish bomba. (Image credit: Wikimedia Commons)
Even more amazing, Rejewiski conceived and built an early electro-mechanical computer, called a bomba, that could be programmed to automate the process of trying these different rotor settings. Bomba might have referred to the bomb-like ticking sound their code-cracking machine made, or perhaps it referred to a dessert the Poles enjoyed eating. Like many aspects of this secret history, no one knows for sure.
By 1938, the Polish cryptologists were routinely reading hundreds of messages a month! Their luck soon changed.
The British Are Coming: Turing and Welchman
In 1939, the Germans made major changes in their methods for transmitting messages and, more devastatingly, they added two additional Enigma rotors. The Polish resources were stretched thin at this point and, without more financing and staff, their prospects for cracking the newly empowered Enigma were bleak.
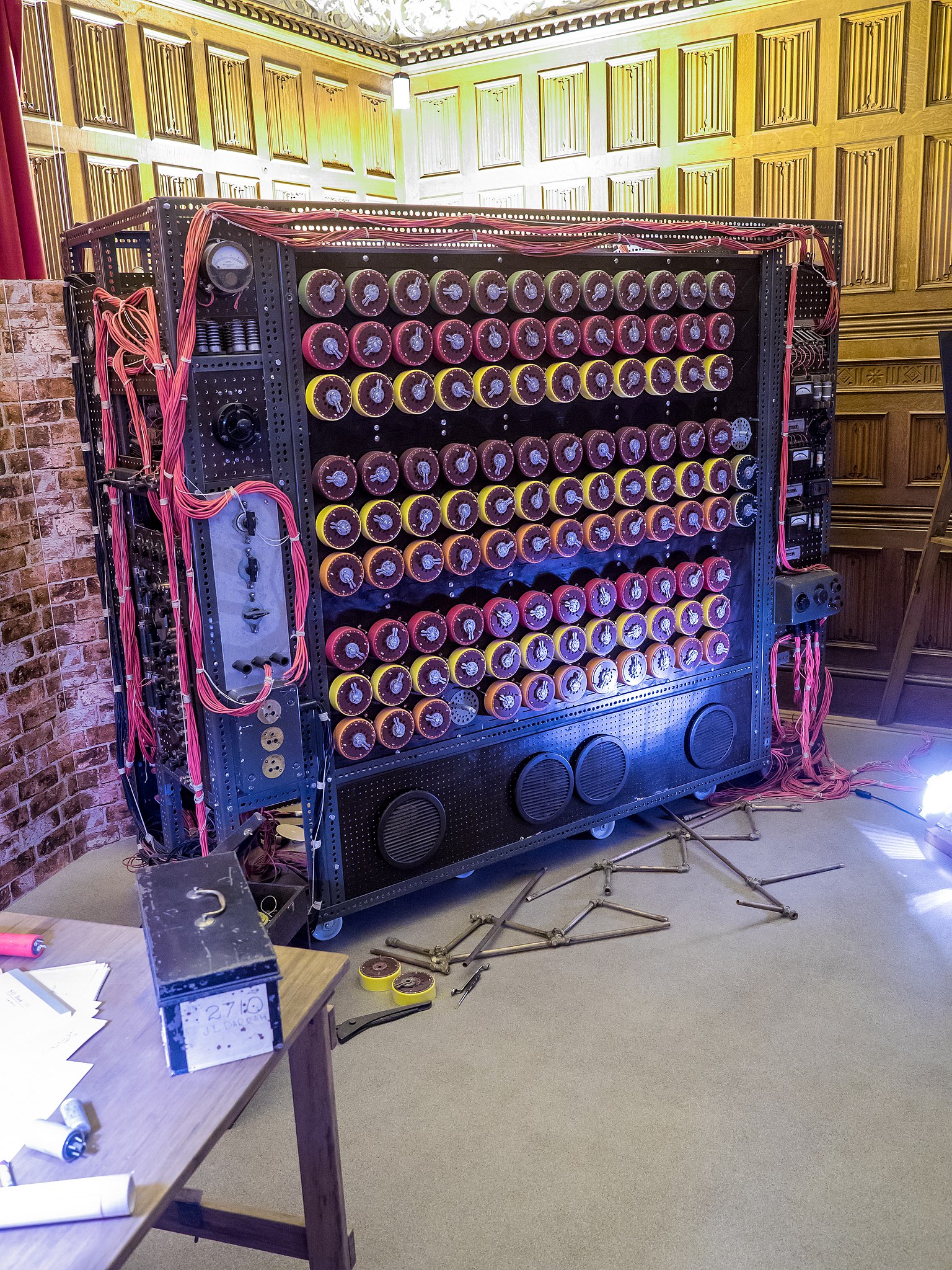
Replica of the Turing-Welchman bombe at Bletchley Park. (Image Credit: Wikimedia Commons)
The always-alert Bertrand stepped in and organized a historic meeting between the Polish and British cryptologists near Warsaw in the summer of 1939. The British were dumbfounded when the Poles presented them with a reverse-engineered Enigma and explained their successes in reading German messages.
Dilly Knox, the lead cryptographer and a classics scholar, was reported to have been quite angry at the Poles’ success. Knox represented an old-school approach to cryptography, and he was facing in Rejewski, and later with Turing, a new generation of mathematicians and proto-computer scientists who were better suited to unraveling the newer codes. However, Knox later sent the Polish codebreakers a silk scarf printed with a horse-racing scene – a gentlemanly admission that he had lost the “race.”
The British returned to Bletchley with two Enigmas and Rejewski’s extensive documentation. Soon after this incredible meeting, the Nazis invaded Poland, forcing the Polish team to flee to France, where they eventually made their way to Bertrand’s group. Interestingly, Rejewski met briefly with Turing in Paris. Turing, known for being sparing with his compliments, came away impressed with the Polish cryptographers’ work. But, to Rejewski’s bewilderment, he and his colleagues were to have limited contact with – and to receive little recognition from – the British during the war.
After the meetings with the Poles, British codebreaking suddenly went into high gear. Turing and mathematician Gordon Welchman were enlisted to help at Bletchley. The story now starts to resemble The Imitation Game. By 1941, Turing’s design for a working bombe was in production – it was a more powerful, “industrial” version of the Polish bomba. As the Poles had earlier discovered, Turing realized he could harness many Enigma rotors in a guided attack on an encoded message.
The Imitation Game also overlooked Gordon Welchman’s accomplishments (or more accurately, misattributed them to chess master Hugh Alexander) in radically improving the efficiency of the bombe. In fact, it’s officially known as the Turing-Welchman Bombe. Because of the secrecy still surrounding Bletchley, we continue to discover more of Turing’s code-breaking secrets as new documents are declassified.
After the war, Turing was horribly mistreated by the British government and was ultimately driven to suicide – our MagellanTV documentary about Turing fills in the details of his final years. Welchman eventually moved to Massachusetts to work for the U.S. military and, when he decided to write a book about the Bletchley codebreakers in the 1980s, National Security Agency harassment led to a downward spiral in his life. Rejewski was never fully acknowledged even in Poland, and he accepted a job as a college mathematics instructor, staying far away from cryptology. Finally, those who worked at Bletchley were under oath not to reveal their war-time experiences. Many still complied even after some of their secret work began slowly to be revealed, starting in the 1970s.
It seems a codebreaker’s life and work, if it were left solely to the intelligence services, would remain secret – almost as if they could be erased like an old data file. Thankfully, we have a few books and technical articles from eyewitnesses, principally Welchman, Rejewski, and Bertrand, that allow us to see some of the larger picture. The rest may forever remain hidden from the public and lost to history.
Ω
Title Image: Bombe Machine at Bletchley Park (Image Credit: Mendhak/Creative Commons)

